The Invisible Bodyguard: Why Zero-Trust is the New Standard for Patient Trust
27 Jan 2026 By: Maria Rush
Updated
I’ve spent the last couple of years helping business owners build remote teams. I can tell you that the number one thing that keeps healthcare providers awake at night isn’t the cost of labor. It’s the fear of a data breach. When you are outsourcing, should know that part of it is handing over the keys to your patient data.
If you want to sleep better, you need to understand something called zero-trust. I like to call it the “Invisible Bodyguard.” It is the only way to handle cybersecurity in healthcare today.

The High Cost of “Trusting” the Wrong Partner
Before we get into how it works, let’s look at the reality of the situation in 2026. According to the latest IBM reports, healthcare has the highest average breach cost of any industry for the 14th year in a row. In the United States, the average cost of a single healthcare data breach has hit a record $10.22 million.
Even more alarming for those of us in the BPO world is that 35.5% of all data breaches now come through third-party vendors. Attackers aren’t always breaking down your front door. They are logging in through your partners’ credentials because those partners didn’t have the right security in place. This is why cybersecurity for healthcare cannot be an afterthought.
What is Zero-Trust Cybersecurity in Healthcare?
When people talk about zero trust, they usually make it sound complicated. It really isn’t. The core idea is simple: never trust, always verify.
In the old days, we used a “castle and moat” strategy. You built a big wall around your office network. If someone was inside that wall, you trusted them. But that doesn’t work anymore. With remote work and cloud systems, there is no “inside” anymore. Zero-trust assumes that the “bad guys” are already trying to get in, so it checks everyone’s ID every single time they try to touch a file.
Why is the “Castle-and-Moat” Model is Failing?
I have seen this happen too many times. A practice has a great firewall at their physical office. Then, an employee takes a laptop home or a hacker steals a password. Suddenly, that person is “inside” the moat. Since the system trusts them, they can move around and look at everything. They can see billing, clinical notes, and patient IDs.
Healthcare cybersecurity has to be better than that. You can’t have a system where one stolen password gives a hacker the keys to the entire kingdom.
The Zero-Trust Difference
| Feature | Traditional Security (Old Way) | Zero-Trust (The HelpSquad Way) |
| Trust Level | Trusted by default once logged in. | Trust is never assumed; always verified. |
| Access Range | Full access to the entire network. | Least Privilege: Access only to specific tools. |
| Verification | Single password (often weak). | Multi-Factor Authentication & Biometrics. |
| Reaction | Detects breach after it happens. | Prevents movement during an active breach. |
The 3 Pillars of the “Invisible Bodyguard”

For a healthcare provider, Zero-Trust acts as a silent protector that works in the background of every patient interaction. When we set up our teams at HelpSquad, we don’t just hope people are doing the right thing. We use a system that makes it impossible for them to do the wrong thing. This is how cybersecurity for healthcare actually works in the real world.
1. Identity-Based Security
It doesn’t matter if the virtual assistant is in the Philippines or sitting in a desk in Pennsylvania. Their “location” isn’t what makes them secure. Their identity is. We use Multi-Factor Authentication (MFA) and sometimes biometrics. The system constantly asks: “Are you really who you say you are?” before it lets them do anything.
2. Least Privilege Access
This is a big one for me. You should never give a remote worker more access than they need to do their job. If I hire someone to handle your scheduling, they don’t need to see the patient’s full medical history. In a zero-trust setup, they only see the calendar. If they try to look at a clinical note, the “Invisible Bodyguard” blocks them.
For example:
- The Billing Specialist can see insurance codes but cannot see the doctor’s private clinical notes.
- The Appointment Scheduler can see the calendar but cannot export the entire patient database.
3. Micro-segmentation
Think of this like a hotel. Your room key opens your door, but it doesn’t open the door to the room next to you. We break the data into tiny zones. If one person’s computer gets a virus, it stays in that one “room.” It can’t spread to the rest of your EHR or your billing system.

What is the Value of Zero-Trust in Your Practice
Patients in 2026 are highly aware of data privacy. A remote team running on a zero trust framework is often much safer than a local office where passwords are on sticky notes.
When you tell your patients that you use cybersecurity for healthcare that follows these rules, you are building a massive amount of trust. You are telling them that you care enough about their privacy to use the best technology available.
The value for your practice:
- Reduced Liability: Minimizes the “blast radius” of any potential cyber incident.
- Scalability: Hire global talent at a lower cost (like HelpSquad’s $8/hr specialists) without compromising the security standards of a major hospital.
- Compliance: Meets and exceeds the evolving requirements for HIPAA and cyber-insurance policies.
How to Audit Your Outsourcing Partner
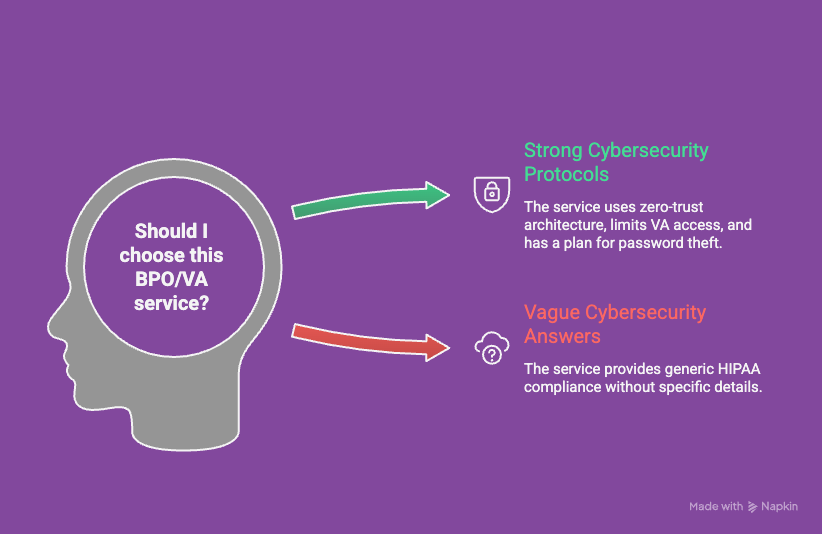
If you are looking at a BPO or a VA service, you need to ask them about their healthcare cybersecurity protocols. Don’t let them give you a vague answer about “being HIPAA compliant.”
Ask them specifically:
- Do you use zero-trust architecture?
- How do you limit what my VA can see?
- What happens if an agent’s password is stolen?
If they can’t answer those questions, they aren’t protecting your practice.
Conclusion: Protecting the Patient Relationship
At the end of the day, healthcare is about care. By implementing Zero-Trust through a strategic outsourcing partner, you aren’t just checking a compliance box. You are deploying an “Invisible Bodyguard” that ensures your patients’ most private information remains just that private.
Ready to Secure Your Practice?
If you are looking at a BPO or a VA service, you need to ask them about their healthcare cybersecurity protocols. Don’t let them give you a vague answer about being HIPAA compliant. Ask if they use zero-trust architecture and how they limit what an agent can see.
At HelpSquad, we’ve already built the “Invisible Bodyguard” for you. We provide the elite security of a major hospital group at a price point that makes sense for independent practices.
Let’s talk about how we can support your team while keeping your data locked down. Talk to Us.
Frequently Asked Questions
What is the purpose of zero trust?
The goal is to protect your patient data from modern hackers. Instead of one big fence around your office, it puts a security guard at every single door inside your network. This prevents a thief from moving around even if they steal a password.
What is the main assumption in a zero trust approach?
It assumes the “bad guys” are already on your network. We stop trusting the “perimeter” entirely. Every user and device must prove their identity every single time they try to open a file or a program.
Why is it called Zero Trust?
It gets this name because trust is never the default. In the past, being on the office Wi-Fi meant the system trusted you. Now, trust is never granted based on your location. You start with zero access and earn it through verification.
What are Zero Trust best practices?
First, use Multi-Factor Authentication (MFA) for every login. Second, use “Least Privilege” access so staff only see the bare minimum files needed for their job. Third, keep a constant log of exactly who touched what data and when.
How do I ensure the accuracy of the information in this article?
ou can verify these facts by looking at the IBM Cost of a Data Breach Report or the HIPAA Journal. We use the latest HHS guidelines to make sure our security standards are correct. Always ask your IT provider for specific proof of how they verify remote identities.


